Security is essential for many apps because they contain critical information about the clients. In this article, we look at the ways to ensure the safety of user data in the mobile app sector.
Modern hardware offers a large number of positives to the users. For example, it helps with processing tremendous amounts of data. This aspect is, however, also a major downside. Since mobile apps store tremendous amounts of data, any problems with security can lead to major leaks. Regrettably, such data leaks are extremely common. In this review, we look at mobile app security and the aspects that help developers ensure the long-term safety of the users.
What is Mobile Application Security, and Why is it Important?
Mobile app security refers to the measures and practices taken to protect mobile apps from threats and vulnerabilities. According to Fortinet, it’s about safeguarding the app’s data, user information, and functionality from unauthorized access, hacking, or misuse. Mobile app security is vital because cybercriminals increasingly target mobile devices. Breaches in security can lead to sensitive information being stolen, such as passwords or credit card details. This may result in financial loss and identity theft. By implementing robust security measures, such as encryption, secure authentication, and regular updates, mobile app developers ensure the safety of user data and enhance their trust.
Common Mobile App Security Risks

What are the key elements threatening mobile app security? In this regard, you should pay attention to the following aspects if you want to ensure your app offers maximal long-term security:
#1: Malware: Malignant Apps
The first problem in mobile app security is the presence of ‘malignant’ programs. Malware is malicious software designed to disrupt, damage, or gain unauthorized access to computer systems, networks, or mobile devices. It comes in various forms, including viruses, worms, Trojans, and spyware. For example, a virus can infect a computer and replicate itself to spread to other files or devices, destroying user data or forcing some intrusive advertisements (Imperva security company calls such attacks malvertising). Spyware can secretly collect personal information from a device without the user’s knowledge. Hackers who promote malware for ‘fun’ are also common: some apps bring about damage for the sake of damage.
#2: Ransomware: Encrypting User Data
One of the key aspects of mobile app security is data preservation. More and more users store vital information about their lives on mobile phones. Many people share data on their finances and health. In this light, a leak of information can lead to major damage for an involved person. Criminals can use health data to, for instance, destroy the reputation of a user (in case the illness has some stigmatized elements to it). Ransomware targets exactly this issue for many users. What does ransomware entail? In this regard, this is malware that infects a phone and then encrypts the data of the user. To get their information back, the victims have to pay a certain ransom, which will give them access to the decryption password. What does this information mean for a mobile app security checklist? It signifies that one has to invest in decryption tools for the common malware and, more importantly, warn the users about the need to minimize the usage of sensitive information and back up the key data. This aspect is critical for security: VentureBeat notes that 83% of the affected companies pay criminals to stop a ransomware attack.
#3: Cryptojacking: Illicit Mining Networks
Cryptojacking is a form of cyber attack where a hacker secretly hijacks someone’s computer or mobile device to mine cryptocurrencies without their consent or knowledge. It involves using the device’s processing power to solve complex mathematical problems and earn digital currencies like Bitcoin. This attack can slow down the device, drain its battery, and increase electricity costs. For example, a hacker may embed malicious code in a website or email, and when the user clicks on a link or opens the email, their smartphone becomes a part of a network of compromised devices mining cryptocurrencies for the attacker. Such an issue is especially damaging for mobile app security because these devices are less adjusted to long-term mining. While PC hardware is created with 24/7 work in mind, mobile phones involve more sporadic use. Cryptojacking can disrupt expensive devices in a short time span, considering such an issue. The problem is serious enough that major publications such as MakeUseOf offer guides that help with detecting and avoiding crypto-mining attacks.
#4: Insecure Coding: Compromised Code
Insecure coding refers to the practice of writing software code that contains vulnerabilities. Such a problem results from irresponsibility or, more importantly, lack of experience. Some companies, regrettably, cut corners by giving vital tasks to junior developers, for instance. This is the reason why one should make a major investment in the improvement of the workforce. Examples of insecure coding include not properly validating user input, not implementing encryption for sensitive data, or not securely handling error conditions. If you’re interested in a company that doesn’t try to save funds on mobile app security, you can address us. We have a strong team of middle and senior developers who know how to provide high-quality products for you.
Mobile App Security Checklist: How to Secure Mobile Apps?
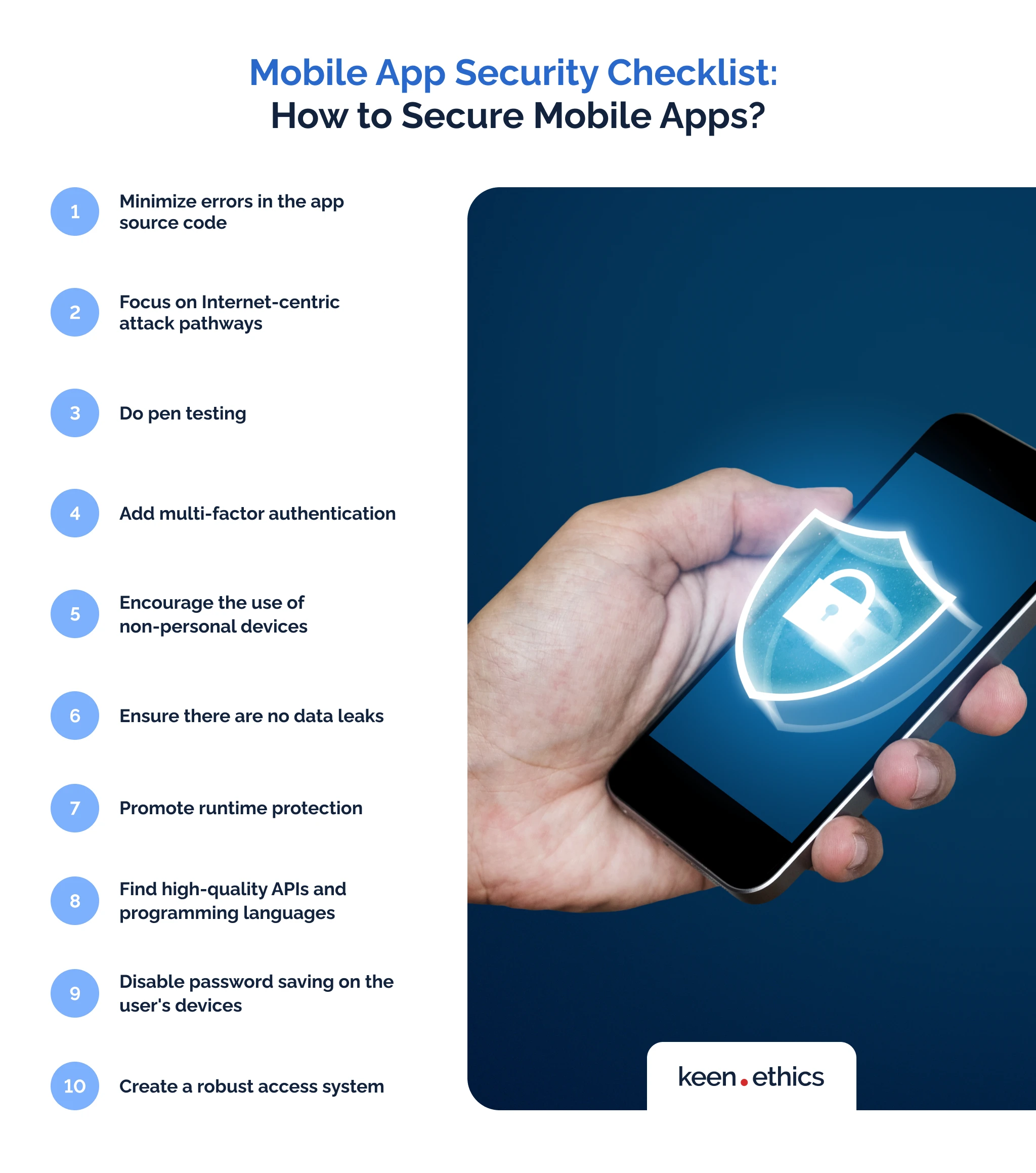
Now that we know the potential problems affecting mobile app security, it’s time to analyze how to ensure it in the long-term scenarios. In this regard, we offer a full-scale mobile app security checklist. Let’s review the key measures to consider:
1. Minimize errors in the app source code
A major source for many hacks is the presence of bugs within a mobile app’s code. These errors manifest in diverging aspects of app functioning: they can involve some interactions with the interface or data leaks during the connection to the Internet. What should you do at this stage? Firstly, it’s crucial to invest in the specialists. The vital parts of code that can be the most vulnerable to attacks from perpetrators should receive attention from at least middle developers with significant experience (and, better, senior developers). Secondly, one should perform periodic code reviews to guarantee errors are minimized. Even the best coders make major mistakes. If you’re interested in ensuring mobile app security this way, our company is out there to assist. We can perform an audit of your code and help you with closing the key gaps within it.
2. Focus on Internet-centric attack pathways
How to ensure maximal security even for devices without major precaution measures? You shouldn’t connect it to the Internet. Obviously, such an approach is impossible in the modern world: the whole point of smartphone devices is that they can connect to the Internet. What should you do to ensure mobile app security in such a situation? One should add as many failsafe frameworks for Internet connections as possible. What do we recommend? Invest in encryption and pay specific attention to the code related to online-centric connections. Use technologies that make it possible to minimize data leaks during the communication between the app server and the client.
3. Do pen testing
Pen testing, short for penetration testing, is a method of assessing the security of computer systems, networks, or apps. It involves simulating real-world attacks to identify vulnerabilities and weaknesses that malicious hackers could exploit. The purpose is to evaluate the system’s security and recommend measures to enhance its defenses. Why is it important? You get an opportunity to see the functioning of your protection systems in real-life scenarios. Many frameworks seem good on paper but appear inefficient when they manifest in reality. Pen testing is a perfect way to understand if certain ideas are viable.
4. Add multi-factor authentication
A common advice one may give for many activities in life is simple: don’t put all eggs into one basket. In this regard, relying solely on password systems or access confirmation via Internet-based resources is a dangerous framework. Two-factor authentication is a key element in the mobile app security checklist because it spreads protection of the users to multiple technologies with different functioning. What do we mean by this? Password systems use traditional software code for access. Two-factor authentication utilizes many legacy systems, such as SMS and phone calls. A good two-factor authentication framework means that the hackers would have to break into the software-based systems and the relevant hardware.
5. Encourage the use of non-personal devices
This point is important for apps involving information related to various companies. For example, we imply apps that ensure communication within a firm or involve the calculations of some vital company data. What do we recommend in this case? Encourage the users not to install such apps on their devices. In our opinion, separating work and personal use is essential for security. You may have a secure app, but the usage of other software can easily compromise it. Users who install work-related apps on their personal phone risk leaking some vital data if malware capable of making screenshots infects their device. Mobile app security doesn’t only involve technical methods: it also necessitates a clear strategy regarding user behavior.
6. Ensure there are no data leaks
A major problem, even for the most well-protected apps, is the potential data leak due to human errors rather than problems with code. Mobile app security can be compromised after a leak of information about its source code, for instance. How can it occur? Someone may break into your site and server and steal the data. This means high-quality mobile app security isn’t only about making an app protected. You also have to consider the protection of the data that surrounds development. For instance, many projects involve outsourcing, which can end in data leaks. You have to anticipate such potential problems before they occur.
7. Promote runtime protection
Runtime protection refers to the measures and techniques implemented to safeguard software during its execution or runtime. It involves monitoring the application’s behavior, detecting potential threats or attacks in real time, and taking immediate actions to prevent or mitigate them. Runtime protection helps to identify and respond to security breaches, unauthorized activities, or abnormal behavior within an app to ensure its integrity and security. We recommend installing such frameworks in all apps to guarantee maximal security. Anti-tamper methods are essential if you want protection.
8. Find high-quality APIs and programming languages
There’s a harsh saying in mathematics. It goes like this: “garbage in, garbage out.” What does it mean? The quality of inputs defines the quality of the outputs. Regarding app creation, this principle is meaningful. Why? It points towards a factor some people fail to consider: your app depends on the quality of the API and even the internal programming language assembler code as much as on the quality of the code written within the programming language. For example, Salesforce once faced a major data leak due to its APIs, according to ZDNet. In short, an insecure programming language or API is one of the best ways to fail a mobile app security checklist. If you want to develop a product that is secure, you need to concentrate on safe programming languages. In this case, we recommend focusing on frameworks such as Node.js. Our company has major expertise within this platform. You can communicate with us to get high-quality advice regarding this topic.
9. Disable password saving on the user’s devices
The process of managing multiple passwords is annoying. Let’s admit it: we all hate it. In this situation, many apps for storing passwords appear on the market. Some options even allow one to save their password within the relevant software. What’s the problem with this approach? It’s convenient, but it leads to major data leaks. By saving passwords in any fashion, you increase the number of entry points regarding mobile app security. How to solve this problem? Don’t save passwords. This will be uncomfortable for the customers, but the approach is more secure. As one saying goes, better safe than sorry.
10. Create a robust access system
All companies have clear hierarchies within them. Even seemingly ‘horizontal’ frameworks have leaders. In practice, this means it’s safe to deny users access to certain information. A middle-tier employee doesn’t have to possess access to the commercial secrets of a business, for example. Every mobile app security checklist requires a focus on tiered systems. Why? Even if someone gets access to a device of an employee or hacks into an account, they won’t get all data. In turn, you can dedicate more effort to the security of mobile apps for the top managers of your business.
Related Services
NODE.JS DEVELOPMENT COMPANY
Diving into Mobile Security: Variations and Approaches
Now that we have a clear idea of a mobile app security checklist, it’s time to look at some large-scale strategic methods of ensuring long-term mobile security. How do we achieve it? Let’s find out!
#1: Antivirus based on signatures
A common method for protecting against cyber threats is the reliance on past experience. That’s how antivirus systems work: they analyze large databases of information about various types of malware or hacks and use them to inform clients. This method is great for defending against some popular types of malware, but it may fail if the attackers use unique targeted methods. For this reason, you may add antivirus software to your mobile app security checklist, but you shouldn’t rely on it alone. Antivirus defense isn’t the ultimate way to prevent large-scale problems.
#2: AI-based cloud security
A strong way to boost mobile app security is to use novel tools. In this regard, a good option is to look at AIs. What’s their advantage? They allow for analyzing large amounts of data. Sometimes, a series of small facts can point toward big conclusions. This so-called Big Data analysis performed via an AI is a perfect framework for preventing many attacks. AI allows analyzing even the most obscure behaviors within a certain operating system.
#3: Using intermediaries for communication with the customers
The Intermediary Cloud Approach is a cloud computing model that involves the use of an intermediary or proxy service between users and cloud providers. In this approach, the intermediary acts as an additional security layer, managing the interactions and data exchange between users and cloud services. It can provide additional functionalities such as security, privacy, performance optimization, or data transformation. The intermediary may offer value-added services like data caching, load balancing, or encryption. This approach gives users more control over their data and provides an extra layer of security and customization options compared to directly accessing cloud services. We believe no mobile app security checklist can exist without such a framework.
#4: Behavioral analysis
The final element of our mobile app security checklist is the usage of behavioral analysis. Behavioral analysis in mobile app security refers to the process of monitoring and analyzing the behavior of mobile apps to identify and detect suspicious or malicious activities. It involves examining the app’s runtime behavior, network communications, and user interactions to identify anomalies or deviations from expected behavior patterns. By reviewing the app’s activities, security analysts can detect signs of potential threats such as malware, data leaks, unauthorized access, or unusual user behavior. Behavioral analysis helps identify zero-day attacks or new forms of mobile app vulnerabilities that traditional security measures may not detect. It plays a crucial role in enhancing the overall security of mobile apps. This analysis can work around pre-determined patterns or even use AI. We believe that AI-based mobile app security is an inevitable innovation in the upcoming years.
Related Services
MOBILE APP DEVELOPMENT SERVICES
Emerging Patterns: Trends in Cyberattacks and Cyber Threats
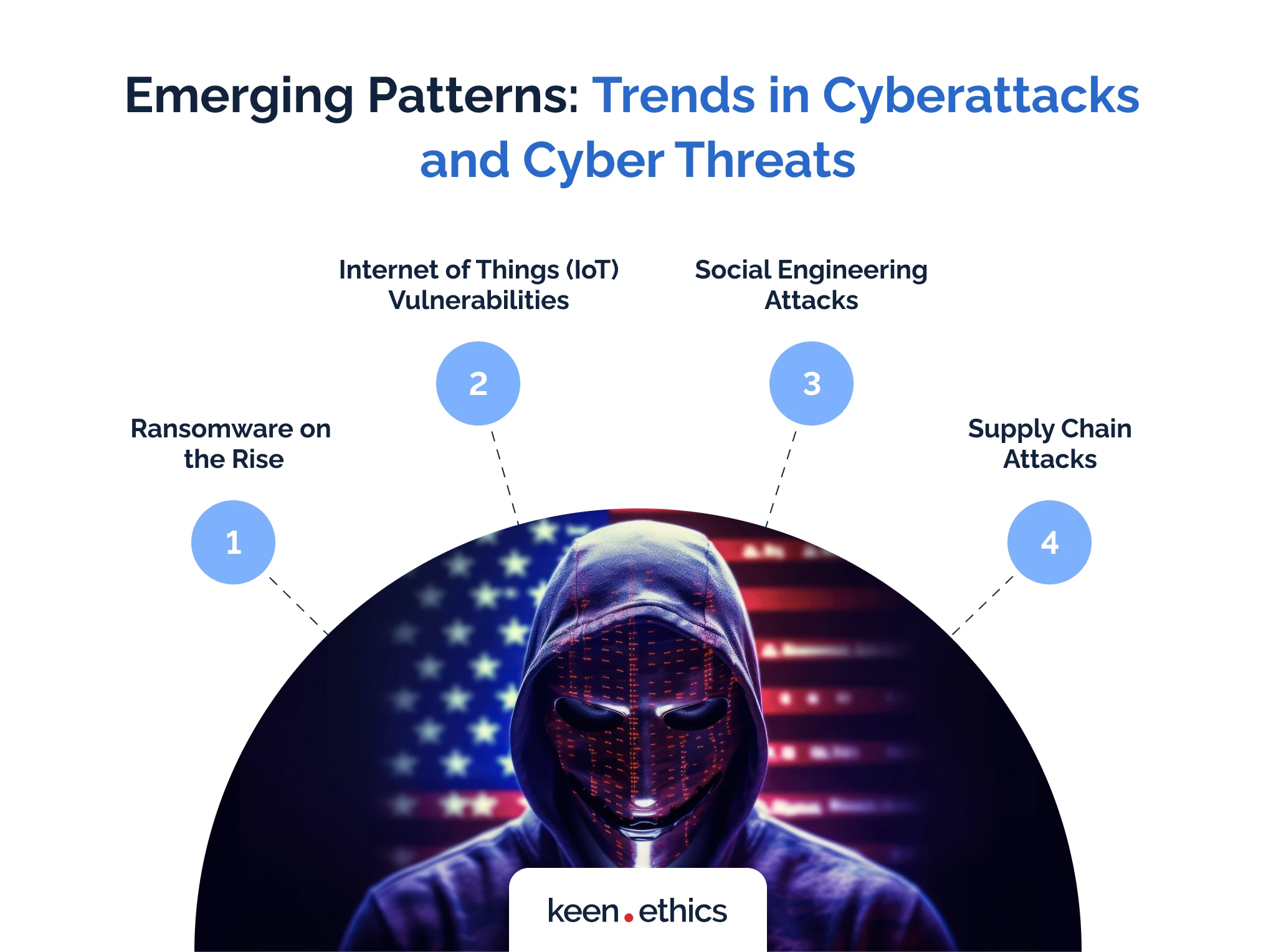
How to secure mobile apps? You have to concentrate not only on the defense methods but also on the threats. Only a thorough understanding of the potential attacks can guarantee long-term security for you.
1) Ransomware on the Rise: ransomware attacks are increasingly prevalent. During them, cybercriminals encrypt victims’ data and demand a ransom for its release. These attacks target individuals and organizations, causing significant disruptions and financial losses.
2) Internet of Things (IoT) Vulnerabilities: with the growing number of connected devices, cybercriminals exploit IoT vulnerabilities to gain unauthorized access or control over devices. Weak security measures and lack of updates make IoT devices attractive targets for attacks. It’s becoming increasingly difficult to track myriads of devices on the market. In our opinion, if you have the option of isolating yourself from IoT devices, such an approach is the best choice.
3) Social Engineering Attacks: Cybercriminals use social engineering techniques, such as phishing emails or fake websites, to trick individuals into revealing sensitive information. These attacks capitalize on human vulnerability and are becoming more sophisticated, posing a major threat to personal and corporate data security. Tricking people is simple: many individuals don’t anticipate any malignant attacks of this kind.
4) Supply Chain Attacks: Cybercriminals are targeting software supply chains to gain unauthorized access to certain organizations. By compromising a trusted vendor or supplier, attackers can inject malicious code into legitimate software updates, which may then be distributed and installed on unsuspecting users’ systems, leading to data breaches. That’s why the best option is to develop secure apps based on the minimum number of side platforms and solely within one development team.
Conclusion
How to secure your mobile app? You must use the most novel technological frameworks and train the users to anticipate attacks targeting human errors. If you want to develop a secure mobile app, don’t hesitate to contact our company. We have several years of experience in the market and know how to develop a secure solution.
Common Questions About Mobile App Security
What technologies are used in mobile app security testing?
Mobile app security testing commonly utilizes techniques such as static analysis, dynamic analysis, penetration testing, and vulnerability scanning.
What should I add to the mobile app security checklist?
Some important items to consider adding to a mobile app security checklist are encryption, secure authentication, secure data storage, and regular security updates.
What are the potential threats to mobile apps (in terms of security)?
Potential threats to mobile apps include data breaches, unauthorized access, malware infections, phishing attacks, insecure data storage, and insecure network communications.
You’ve found the right site to contact specialists who can deliver a secure project.