This article will help you understand your security priorities and take security measures in regular practices.
Node.js security, like all other frameworks or programming languages, is prone to all kinds of web application vulnerabilities. The core of Node.js is secure, but third-party packages may require additional security measures to protect your web applications. According to this analysis, 14% of the Node Package Manager (NPM) ecosystem is affected. The indirectly affected packages are estimated to be about 54% of the ecosystem.
Why Node.js Projects Have Security Risks?
Open-source applications don’t inherit security and licensing issues from their open source components. The problem is that security testing tools like dynamic and static code analysis are ineffective at detecting open source vulnerabilities.
In order to identify open source components in Node.js, you have to analyze the package manager index files describing the dependencies. However, the index files don’t include reused open source components.
The open-source community often reuses open source projects to accelerate development, decrease time to market, and incorporate functionality. As a result, both open-source and commercial developers can introduce functions, code snippets, and methods into files. The result is that many Node.js projects include licensing terms other than the original Node.js license.
Is Node.js a Threat to Safe Application Functioning?
Some developers consider Node.js to be a security threat due to the lack of default error handling, caused by platform construction. Errors or application failures can lead to server turnoffs.
NPM phishing and regular expressions Denial of Service (DoS) is only a small percentage of Node.js security problems.
Alex Pletnov, Chief Technical Officer of Keenethics, provides two main reasons why sometimes we can’t consider Node.js security is under high threat.
Firstly, developers can make mistakes in designing an app like allowing CSRF and cookie stealing. Secondly, developers with little expertise in Node.js can rather accuse Node.js of being unsecured than acknowledge one’s incompetence in technology. In addition, there are the usual web security issues like cross-site request forgery, cross-site scripting, unvalidated redirects, and security misconfiguration.
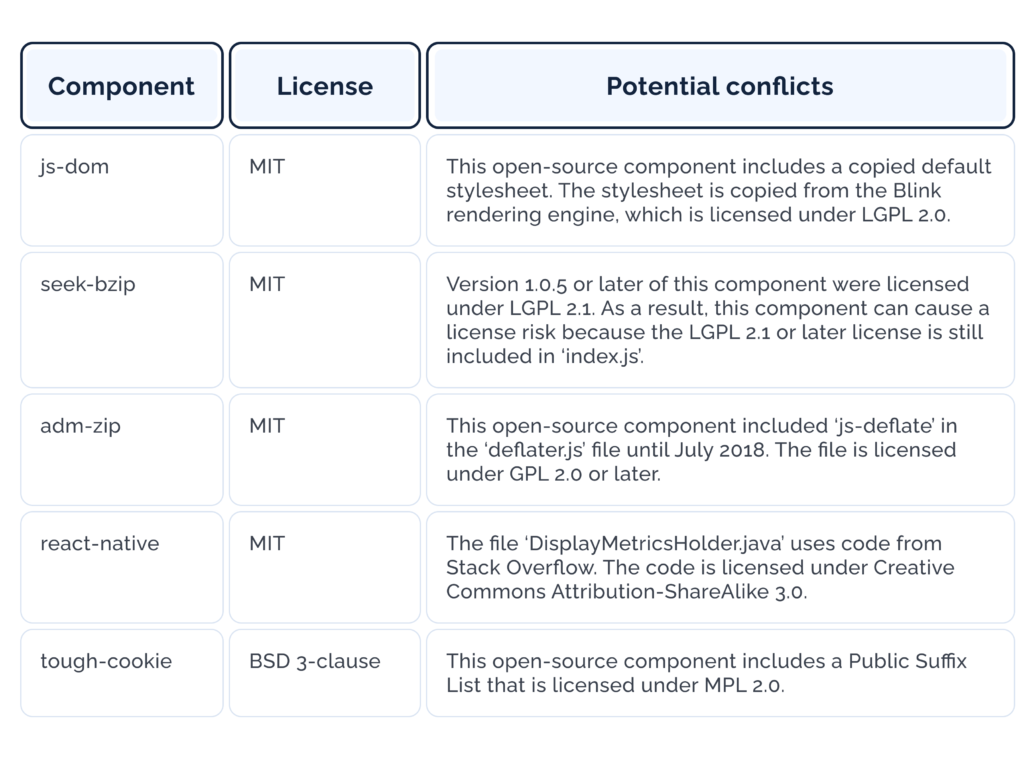
Open Source Components Causing Node.js Security Issues
The following table reviews some of the open-source components you can find in Node.js projects. These components consist of hidden license elements that can cause a Node.js security risk. Failure to comply with hidden open-source license elements can put a company at risk of legal actions.
Top 8 Core Security Risks for Node.js
Node.js security issues can expose you to attacks like code injection, man in the middle, and advanced persistent threats. Below is a brief review of the risks that may lead to these attacks, and possible solutions.
1. Broken access control
Risk:
Usually, web apps have numerous user roles like managers, administrators, moderators, vendors. In comparison to the regular users, these roles have more privileges. Broken access control can appear in two ways, including vertical and horizontal escalation. The first way means the attacker uses the confidential data of the regular user to access administrator-level privileges. The second way may lead to a massive data leak where the attacker uses the personal data of the regular users to access the resources of other users.
OWASP rates broken access control as an easily identified, exploitable, and widespread Internet problem.
Solution:
To prevent this vulnerability, every company needs a central, managed interface to document implemented access control procedures. Another good rule is to deny access to app resources by default to every user. Only legitimate users should get permission to view and modify the app resources. Also, companies should handle access control only on the server side. By conducting constant testing and auditing on access control, organizations can ensure all mechanisms work properly. Such tools as a crash test security suite, HDiv, Immuniweb Discovery, PortSwigger/Burp Suite, and Acunetix help companies get vulnerability reports and guidelines to fight threats and attacks on web servers.
2. Injections
Risk:
Writing secure code with no injections seems to be a simple task, but many pitfalls are there. What if you (developer) use open source packages in the app and aren’t sure if they are secure.
Code injection is a form of attack when an attacker uses an input validation flaw to execute malicious code. Any app using untested code comes under security vulnerability.
Solution:
In order to differentiate the secure and unsecured code, it’s best to apply techniques against code injection. You should avoid dynamic code execution in the app, like language constructs (eval) and code strings (passed to setTimeout or the Function constructor). Serialization can also be vulnerable to attacks, so you need to prevent its usage. Finally, performing dependency scanning will help you analyze and ensure the app isn’t prone to attacks related to third-party open-source components.
3. Cross-Site Forgery Requests (CSFR)
Risk:
CSRF attacks force end users to execute unnecessary actions on authenticated web applications. The targets of CSRF attacks are changes in application state requests because the attacker has no way of seeing the forged request response.
Hackers can trick users into executing unnecessary actions by using social engineering techniques, like sending links via chat or email. CSRF can force state-changing requests like changing email addresses and then transferring funds. For administrative users, CSRF can compromise the entire web application.
Solution:
Preventing CSRF in Node.js requires the use of Anti-Forgery Tokens. Anti-CSRF tokens are used to monitor and validate the authenticity of user requests, and prevent one-click attacks.
4. Cross-Site Scripting (XSS)
Risk:
Cross-site scripting (XSS) is a code injection attack exploiting user input vulnerabilities. During it, malicious actors inject scripts into web pages. In this way, these individuals execute arbitrary code in victims’ browsers. This poses a significant threat, particularly for non-root users who may unknowingly trigger these attacks. As a result, sensitive data can be compromised, leading to serious security breaches. XSS underscores the need for robust security practices to safeguard web apps. Why? It has a tremendous destructing potential, being one of the greatest online security threats.
Solution:
You need to implement stringent security measures if you want to mitigate cross-site scripting. Here, we recommend employing input validation and output encoding. In this way, you can sanitize user inputs and prevent malicious code injection. To be more specific, you should go for the following practices:
• Creating content security policies;
• Validating user inputs;
• Regularly updating security measures.
By adopting these practices, web app creators can fortify their defenses against XSS attacks. Additionally, a good practice is educating users about potential threats and promoting vigilance against brute-force attacks. Knowledge is power in many security contexts. All in all, a combination of proactive measures with continuous awareness efforts helps create a resilient defense against XSS.
5. Regular Expression Denial of Services (REDoS) Attacks
Risk:
Regular Expression Denial of Service (REDoS) attacks exploit vulnerabilities in poorly constructed regex patterns. In this way, they cause excessive computation time and lead to service disruptions.
So, how do they work? These attacks target apps relying on regex for input validation. This factor can potentially impact real users by slowing down or halting services. In this respect, vulnerable code, direct dependencies on unoptimized regex patterns, and inadequate header security contribute to the susceptibility of systems to such attacks. Without proper validation of hostnames returned, attackers can manipulate input. In turn, this approach allows them to trigger prolonged execution times. Ultimately, strengthening authentication policies is essential to mitigate the risk of malicious actor groups exploiting these vulnerabilities.
Solution:
To mitigate Regular Expression Denial of Service attacks, you should implement robust solutions:
• Start by optimizing regex patterns and utilizing specialized libraries to prevent excessive computation times;
• Employ strong header security measures to minimize the risk of attackers manipulating input;
• Regularly update and validate direct dependencies to ensure they’re free from vulnerabilities;
• Implementing multifactor authentication and strong authentication policies adds a layer of security. In this manner, you can reduce the chances of unauthorized access, which can serve as a pathway for this attack type.
• Besides, thorough validation of hostnames returned from external sources is crucial to preventing potential exploits.
Ultimately, organizations can greatly enhance their defenses against REDoS by addressing these aspects.
6. X-Powered-By Header
Risk:
X-Powered-By is a common non-standard HTTP response header. Some scripting technologies include this response by default in the header. Servers have the option to disable or change X-Powered-By response to prevent hackers from targeting a particular technology.
X-Powered-By reveals information about the technology used in an app. As a result, hackers can use X-Powered-By to exploit Node.js security weaknesses.
Solution:
You have to hide the information about the server technology by disabling this header.
7. Distributed Denial of Service (DDoS)
Risk:
Distributed Denial of Service (DDoS) attacks overwhelm online services by flooding them with traffic. This approach, in turn, causes downtime and disrupts normal operations. Common pathways of disruption include amplification attacks and botnets. Their goal is to exploit vulnerabilities in the event loop, security rules, and session token management. These attacks aim to exhaust resources and compromise the availability of a service. Unauthorized access can also be a side effect, as DDoS attempts may serve as a distraction. Without a secure platform and adequate protection measures, organizations remain susceptible to the crippling effects of DDoS attacks. Such an issue greatly raises the risks of financial losses and damage to their reputation.
Solution:
Combating Distributed Denial of Service (DDoS) attacks is impossible without implementing robust solutions. Firstly, employing a reverse proxy can help filter and mitigate malicious traffic before it reaches the target. It may act as a shield against common attacks. Secondly, developing and enforcing stringent security rules helps identify and block suspicious activities that underlie DDoS attacks. Thirdly, session tokens and secure platforms add another layer of protection. As a result, it’s more challenging for attackers to exploit vulnerabilities. Lastly, the practice of regularly updating systems, along with employing rate limiting and traffic monitoring, enhances overall resilience against DDoS attacks. This is the perfect way to ensure the continuous availability and security of online services.
8. Cookie Poisoning
Risk:
Session cookies enable websites to identify users. Any action you do on the website is stored as a cookie. Shopping carts in ecommerce sites are the most common example of this functionality.
The session cookie remembers your selected items on the ecommerce site. As a result, the shopping cart will have these items when you are ready to check out. The new page won’t recognize your past activities on other pages without session cookies.
Using default cookie names is risky because attackers can easily identify these names and threaten your application. This practice is cookie poisoning: a default cookie name can be used to hijack your cookie and turn it into a weapon against your website.
Solution:
The solution is to use one of the middleware cookie session modules like express-session.
Top 10 Practices for Keeping Node.js Secure
1. Make a Regular Check of Apps for Vulnerabilities
Risk:
Since the Node.js ecosystem comprises various modules and libraries to install, this produces a security issue. Using the code someone has written or used before, you can never be sure that the code is secure.
Solution:
Automated vulnerability scanning will help you detect dependencies with common Node.js security vulnerabilities. You can also use npm audit for primary control or opt for valuable tools such as Retire.js, OWASP Dependency-Check, Acutinex, and WhiteSource Renovate.
2. Conduct Strong and Complete Authentication
Risk:
Another common vulnerability is an insufficient, weak, or unsteady authentication system. You can execute and bypass this vulnerability by implementing the suggested solution below.
Solution:
Many existing solutions allow you to improve authentication. Some of these tools are Firebase Auth, OAuth, and Okta. Also, you can adopt native solutions. It would be best to use Scrypt or Bcrypt instead of a built-in crypto library when making passwords. Then, 2FA authentication, along with modules like Speakeasy or node-2fa, is another good solution for session processing that can significantly enhance your app security to a new level. Finally, you need to limit failed login attempts, and in case of an incorrect username or password, you should never notify users about this.
3. Limit Payload Size
Risk:
When the body payload is too big, your single thread works harder in processing it. It allows attackers to break servers with a small number of requests.
Solution:
You can either limit the size of incoming requests or configure express body-parser so that it accepts only small-size payloads. If you don’t consider this solution, your app will handle large requests without accomplishing other critical work. In turn, it can lead to low performance and many vulnerabilities to DO.
4. Avoid Data Leaks
Risk:
You need to always control what comes from the front-end and what you will send to it. On the one hand, you can easily send the required information to a concrete object to the front-end and filter the displayed information there. On the other hand, it’s an excellent chance for a hacker to get the confidential data sent from the back-end.
Solution:
This solution requires more work, but it’s worth it. A good practice is to send only needed information and control everything you want to show. Since all confidential data is easily accessible via browser developer console, you need to retrieve everything from the database to prevent data leaks.
5. Establish Logging and Monitoring
Risk:
You can notice some hackers without logging in. However, some of them prefer to remain undetected for an extended period.
Solution:
So, when you monitor logs and metrics, it’s far easier for you to spot wrong matters and prevent breaching your data. Only by establishing logging and monitoring can you understand the source of weird-looking requests: your app, a third-party API, or an attacker.
6. Always Replace Default Cookie Names
Risk:
Cookie poisoning poses a threat to the security of applications built on Node.js, particularly when default cookie names are retained. Attackers exploit predictable names to manipulate or hijack cookies, compromising user data and session integrity. This vulnerability can lead to unauthorized access, data breaches, and potential code-based attacks. Additionally, code duplication in default cookie names across various applications increases the risk, as a single compromise could impact multiple services. Relying solely on default names creates a security gap that necessitates a proactive approach to safeguard against cookie poisoning.
Solution:
Mitigating cookie poisoning involves replacing default cookie names through a comprehensive code security auditing process. During the code review process, developers must assess the app code basis for potential vulnerabilities, focusing on eliminating code duplication and ensuring unique, unpredictable cookie names. Implementing this solution enhances the security posture of applications built on Node.js, reducing the risk of cookie poisoning attacks. Regularly updating and monitoring cookie configurations, coupled with continuous code basis review practices, fortifies the defense against such threats, fostering a more resilient and secure environment for user data and session management.
7. Run Node.js as a Non-Root User
Risk:
Running Node.js as the root is a major security risk. Why? This practice grants extensive privileges that could be exploited by malicious actors. Concerns about code injection, Cross-Site Scripting (XSS) attacks, and Cross-Site Request Forgery (CSRF) underline the importance of restricting Node.js processes to non-root users. This is the only way to minimize potential damage and unauthorized access.
Solution:
To enhance Node.js security, it’s crucial to run it as a non-root user. You should implement strict authentication guideline policies, conduct regular code security audits using a reliable code review tool, and address concerns about code injection and XSS vulnerabilities.
What’s the best way to do that? In our opinion, the adoption of a non-root user approach mitigates the risks of unauthorized access stronger than other methods. This is the best way to improve the overall security posture of Node.js apps. Such an approach aligns with the best security practices. Thus, it ensures a more robust defense against various cyber threats.
8. Avoid Blocking the Event Loop
Risk:
If you block the event loop in Node.js, you can cause performance issues and hinder app responsiveness. This act can provoke delays in handling incoming requests, potentially resulting in degraded performance or timeouts.
Solution:
To maintain optimal performance in Node.js apps, avoiding the blocking of the event loop is essential. What should you do to achieve this? Firstly, implement non-blocking asynchronous code, utilizing features like callbacks and async/await. In this respect, developers should prioritize efficient coding practices and conduct thorough code reviews. Secondly, employ strategies such as microservices architecture and load balancing. They help distribute workloads, preventing single points of failure and enhancing overall app responsiveness. By adhering to non-blocking principles, Node.js apps can handle concurrent operations effectively. In the end, this process ensures a smoother user experience and improved system efficiency.
9. Pay Attention to HTTP Headers
Risk:
If you overlook HTTP headers in web apps, there’s a risk of security vulnerabilities. Why? Headers play a crucial role in communication and security policies. Ignoring these details may expose apps to risks like Cross-Site Scripting and unauthorized access.
Solution:
Prioritizing attention to HTTP headers is essential for robust web app security. Developers should diligently set and validate headers, implementing strict security policies. Here are some core practices to consider:
• Regular code reviews;
• Utilizing tools for static analysis;
• Integrating security practices into the development lifecycle;
• Emphasizing secure configurations, such as Content Security Policy (CSP) headers.
All these practices help identify and address potential header-related vulnerabilities. By actively managing HTTP headers, developers enhance the security posture of their apps. In turn, this prevents potential exploits and fortifies defenses against a range of security threats.
10. Validate User Input
Risk:
A failure to validate user inputs enables attackers to exploit vulnerabilities through injection attacks. To be more specific, inadequate input validation opens a path for Cross-Site Scripting (XSS) and similar practices.
Solution:
In our opinion, validating user input is critical for robust app security. In this regard, developers should implement thorough input validation checks. They can ensure data integrity and prevent injection vulnerabilities. Utilizing appropriate input validation methods, such as whitelisting or blacklisting, is also vital.
What are some other high-yield recommendations? You should conduct regular code reviews and leverage automated testing tools. Why? They can help you identify and rectify potential input validation weaknesses. All in all, developers can fortify their apps against a wide range of security threats by prioritizing comprehensive input validation practices.
Our Experience and Successful Projects
These days, Node.js has proven to be one of the most popular platforms on the web. Keenethics is among those who frequently implement Node.js in developing projects for our clients. One of the successful projects where we adopt the technology is Bookmaker.
Node.js helped us create a proprietary web platform allowing clients to control the book writing process. We also opt for Express.js, React.js development, MongoDB, AWS to develop the platform.
When working out Bookmaker, Keenethics solved such challenges as:
• inconsistent design where we conducted UX audit to evaluate technological constraints and determine the most critical design solutions;
• platform usability where we built an adaptable and transparent system and excluded all barriers in using the product for different audiences;
• structuring where we simplified the writing process of the book and systematized the workflow;
• device compatibility where we created a responsive design;
• data safety where we added validation for endpoints, improved error handling, minified code, added access checkers for each role, used OWASP standards, checked CORS policy, and analyzed npm vulnerabilities;
• the functionality of MS Word or Google Docs we recreated in a short period of time.
Since we constantly develop and grow, we try to implement effective practices to achieve security in development, including security in Node.js.
Conclusion
In this article, we’ve reviewed some critical questions related to Node.js that are topical in 2024 and upcoming years. We analyzed why the risks exist in Node.js projects, components causing security issues, top security risks, and their solutions. Along with that, we discussed our experience in Node.js and one of many projects we developed using mentioned technology.
Node.js security requires a deep dive into the actual source of a third-party package. We recommend you learn more about the open-source package dependencies of your applications and the hidden elements of their licenses. In addition, you can also address the Node.js vulnerability concerns by leveraging dedicated security tools and audits.
It’s not always obvious what needs to be done when security issues appear. For this reason, use our advice, and you’ll be able to prevent vulnerabilities in your projects. Since we’ve not presented the ultimate list of node.js security best practices, we suggest you view the full node.js security guide. We’ve presented our list of best practices to help you understand your security priorities. We hope you find this article helpful. However, if you still have some questions, talk to us, and we’ll help you make security a best practice.
FAQ
Is it safe to use Node.js?
Yes, experts generally consider Node.js safe when used with proper security practices. Its event-driven, non-blocking architecture can enhance performance, but developers must pay attention to security concerns. Practices like regularly updating dependencies, conducting code security audit processes, and adhering to the principle of the least privilege help mitigate potential risks. In this respect, the Node.js community actively addresses vulnerabilities, providing updates and patches. Ultimately, the safety of Node.js applications depends on the diligence of developers in implementing security measures and staying informed about emerging threats.
Are there any ways to hack Node.js?
Understanding potential vulnerabilities in Node.js is crucial for ensuring robust app security. In this regard, it’s vital to acknowledge common attack vectors. Node.js apps may face risks like injection attacks and inadequate input validation. To combat them, ethical hackers employ penetration testing and code reviews. Their goal is to help identify and address these issues by focusing on secure coding practices and regular updates. Developers must be vigilant against issues such as insecure dependencies and ensure comprehensive security measures. Ultimately, professionals can fortify Node.js apps against potential threats by staying informed and proactive.
What are some core Node.js vulnerabilities?
Node.js applications can be susceptible to various vulnerabilities. For example, injection attacks, like SQL and code injection, may arise from inadequate input validation. In this respect, insecure dependencies and outdated libraries pose risks, emphasizing the need for regular updates and secure configurations. Cross-Site Scripting (XSS) and Cross-Site Resource Forgery (CSRF) vulnerabilities may compromise user data if not addressed properly, too. Lastly, insufficient session management and authentication flaws could also lead to unauthorized access. The process of mitigating these risks involves rigorous input validation and secure coding practices, as well as frequent security audits and vulnerability data monitoring.
How to ensure that Node.js has maximal security?
To maximize security in Node.js, adopt a holistic approach:
- regularly update dependencies to patch vulnerabilities;
- conduct code security audits;
- implement strong authentication mechanisms;
- employ secure coding practices;
- validate user input rigorously;
- guard against injection attacks;
- utilize HTTPS to encrypt data in transit and configure Content Security Policy (CSP) headers to prevent Cross-Site Scripting attacks;
- implement the least privilege principles;
- employ tools for static and dynamic code analysis;
- monitor logs for unusual activities;
- conduct penetration testing;
- engage the Node.js community to stay informed about emerging threats;
- foster a security-conscious culture for developers;
- guard against injection attacks.
Keenethics is amongst the leading Node.js development company with a team of Node.js developers delivering high-quality solutions. We have the high professional expertise to help you prevent security risks from conception to production. Contact us and bring your idea to life.
Thank you to Gilad David Maayan for contributing this article. Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Samsung NEXT, NetApp, and Imperva, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership.